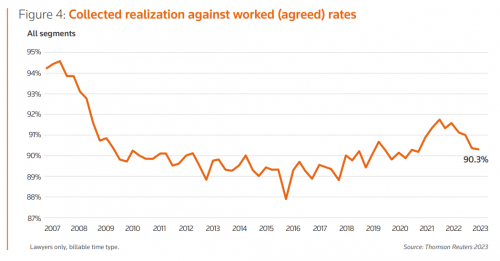
Law firm billing can be either the bane of a lawyer’s career or the reason their law firm gets paid — it’s up to the lawyer themselves to decide. Thankfully, it’s easier to implement legal time tracking software into a law firm’s operations than most think. Legal software can help lawyers simplify the billing and invoicing process, creating a space where clients know expectations and trust the statements. This is especially vital in an environment where finances are a sore spot.
Clients continue to push back on rate increases and look for more discounts, according to a recent analysis of the legal field. As attorney rates continue to increase, clients are weighing their options and searching online for lower-cost counsel.
Importance of Legal Billing Guidelines
Getting paid has more to do with a firm than it does with its clients. If a client refuses to pay an invoice or they decline to pay on time, it means the firm has missed several vital signals — potentially going back to when they first took on the client. The problems that created their unwillingness to pay could’ve occurred a long time ago.
Let’s take a look at a fictitious firm, Woolford and Woolford SC, to show an example.
- Woolford isn’t positioned as an expert in their local marketplace, so clients see them as a discount provider.
- Their business development tactics rely on needy language that attracts price shoppers.
- They’re desperate for work, so they welcome these clients into their firm.
- Their intake process is inadequate; they don’t realize they should interview clients, set expectations, and establish/assess billing guidelines.
- These clients complain about Woolford’s invoices; they refuse to pay for research, administrative expenses, or junior associates in their firm.
- Partners in Woolford are conditioned by their clients to expect rejection, so they add discounts, write-downs, and write-offs to their client’s invoices preemptively.
- The partners are desperate to keep their client, so they offer more. Realization rates fall as revenue and profit decline.
Many law firms deal with a similar scenario, in one form or another, daily. Clients — not firm partners or attorneys — determine what they’ll make. Yes, law firms set their rates, but ultimately, this holds less value if clients are unable or unwilling to pay.
Get Paid Faster With These Law Firm Billing Best Practices
These best practices aren’t a cure-all. Clients won’t pay law firms if there’s a legitimate reason for them to hold back. However, law firms that implement these best practices will find a large amount of non-payment issues resolved overnight.
Let’s take a look.
Law Firm Billing Best Practices #1: Build a Powerful Brand
Branding is commonly misunderstood by businesses, partners, and even marketers. Many believe that their “brand” is a promise, their product or service, their website, or even their logo — it’s not solely one of those things. On a larger scale, branding is your reputation. It’s the gut feeling people have about a specific law firm.
With many lawyers focusing on practicing law, most attorneys and law firms haven’t built or budgeted for a brand. Without a clear brand, most clients can’t tell the difference between one firm and its competitors.
Clients aren’t typically familiar with the legal industry, so they can’t assess another firm the way most legal professionals can. Clients will rely on other signals to make their decision — personal recommendations, reviews, first impressions, and price.
To fix this, law firms need to build a powerful reputation in the hearts and minds of prospective clients. There are some simple principles you can use to guide you:
1. Do what your competitors can’t or won’t do.
Become an expert in a specific practice area, win a large number of cases, achieve the impossible in a real estate negotiation. Find a way to become exceptionally known for something.
2. Create value for everyone, all the time.
Attorneys can solve problems for those around you by giving speeches, writing articles, hosting webinars and events, and serving the community, creating a powerful and valuable resource. Find a need, then solve it like no one else.
3. Promote your achievements.
Share accomplishments with others in a way that says, “I did this for clients just like you, I can do it for you too.” This is the essential crux of business development, but it’s also the main component most attorneys and firms miss. Lawyers can build a strong website, run a legal blog, or interact with their community on social media.
4. Build partnerships with other influential legal professionals.
As lawyers begin to achieve the above items, they’ll start to build a brand (reputation). Use this reputation to develop successful relationships with powerful, like-minded supporters who are interested in the value provided.
Doing this attracts an avalanche of clients. Marketing and advertising campaigns outperform competitors at a lower cost per click/visit. Firms can attract more clients than other similar practices.
These clients have seen the value provided, and they’re eager to work together. Once a firm is differentiated in their mind, they want that specific firm. As a result, they’re respectful, hopeful, and willing to pay the higher fees requested. The brand precedes the firm.
Law Firm Billing Best Practices #2: Verify Employee Timekeeping
Without a proper legal billing policy in place, money is left on the table. The team is left to track their time on a whim. They’re prone to human error and estimating their time. The longer timekeepers take to complete their timesheets, the more billable leakage their firm experiences. Ann Guinn shared research that supports this in her ABA blog post:
- You lose 10% of your revenue (billable time) if you record time entries the day of once a day.
- You lose 25% if you wait 24 hours to record your time.
- You lose 50 to 70% if you wait just one week.
The attorneys in this particular case study were waiting until the end of the month! If this is projected out, this means firms could be losing 200% to 280% of the revenue they should have. Income that’s rightfully theirs simply because they didn’t track their time correctly.
Here’s how you fix this.
- Switch to automated time tracking software: Legal time tracking software like Bill4Time provide automatic time tracking that accurately captures time. This “set it and forget it” software limits human error and stops revenue leakage.
- Appoint a legal billing liaison: This could be a managing partner, director, or executive that’s responsible for managing the firm and keeping everyone knowledgeable of procedure. This legal billing liaison can create ad sample attorney billing descriptions to help firm staff write better billing descriptions.
- Create an incentive system: Once a new legal billing policy is in place, it may be difficult for everyone to jump on board. It would be worth-while to create morale with incentives or awards to take the edge off and make the process a fun competition.
Treat the line items in your invoice as inventory in a store. It’s valuable revenue, and it needs treatment as such.
Law Firm Billing Best Practices #3: Follow Through With Legal Billing Guidelines
Once a law firm and its clients have agreed on legal billing guidelines, follow them to the letter. Doing this bolsters trust, decreasing the likelihood of a flagged or delayed invoice. Here’s a brief overview of what these guidelines should look like:
- Shepherd invoices through an eBilling system. If estimates are conservative and there’s a particular emphasis placed on accuracy, pre-bills will be close to the final bill. This attention to detail reduces the need for discounts, write-downs, and write-offs. There’s also a chance to catch billing issues and missed requirements before clients flag them.
- Pick up the phone and call clients any time there’s a disparity. Are you drastically over or under budget? Have you run into an unexpected expense? Reach out to your decision-makers and point-of-contact ahead of time. Don’t ambush your clients with a surprise (positive or negative).
- Resist the urge to discount or write-off time. Treat timesheets like inventory. Remember that each line item on an invoice is a unit of revenue. Think of every improvement made to the quality of timesheets/invoices as improving the acceptance and collection realization rates for the firm.
- Submit invoices on time. Poor communication and law firm sluggishness in publishing invoices is a contributing factor to delayed or decreased payment. Make sure to stick to the schedule and bill clients on time.
- Offer ePayments. Use alternative fee arrangements that ensure fair compensation. Built-in online payments processors like Bill4Time Payments allow firms to safely and compliantly accept online payments. Offering ePayments increases the likelihood that clients will pay firms on-time — and 70% faster.
Take a look inside Bill4Time Payments.
Increase Firm Cashflow With Law Firm Billing Software
Implementing these tips will help boost realization rates, revenue, and profit in law firms. Using law firm billing software, like Bill4Time, to help navigate legal billing can take a practice to the next level.
Schedule a demo with Bill4Time today to see the positive impact it can have on law firm billing.
Editor’s Note: This blog was originally published in July 2021. Last update: November 2023.